
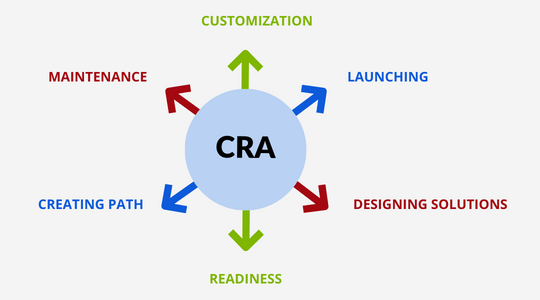
How to Choose the Best Cybersecurity Manager Certification that Truly Matters in 2025:
Introduction: As growth and evolution of early-stage cyber-attacks continue to move at a faster rate than ever, cybersecurity certificates have …

Drive business productivity and efficiency coupled with robust security and confidence using our end-user protection services





Endpoint protection is the process of stopping unauthorized agents and campaigns from targeting endpoints or access points of end-user computers such as desktops, notebooks, and handheld devices. Cybersecurity risks are secured by endpoint security services on a network or the internet. Endpoint security has advanced from antivirus tools to robust defenses against complex ransomware and new zero-day attacks.
Nation-states, hackers, organized crime, and deliberate and unintended insider attacks pose a danger to companies of all sizes. Endpoint security is often referred to as cybersecurity’s frontline, and it is one of the first areas that companies look to protect their networks.
The market for more sophisticated endpoint protection technologies has risen in parallel with cyberattacks’ volume and complexity. Endpoint security solutions today are designed to easily detect, evaluate, prevent, and contain active threats. To do so, they must work together and with other security tools to provide administrators with insight into advanced threats, enabling them to respond quicker to identification and remediation.
For a variety of purposes, an end-user defense framework is an integral component of enterprise cybersecurity. First, in today’s business world, data is perhaps a company’s most important asset—and losing that data or access to certain information could put the entire company at risk of insolvency. Businesses have had to deal with an increase in the number of endpoint forms and an increase in endpoints. On their own, these factors make corporate endpoint protection more challenging, but they’re aggravated by remote work and BYOD policies, which render perimeter security ineffective and reveal vulnerabilities. Also, the threat environment is becoming more complex:
Hackers actively devise new strategies to obtain access, steal information, or persuade workers to divulge confidential information. When you consider the opportunity cost of redirecting resources from business priorities to risks, the reputational cost of the huge breach, and the real financial cost of enforcement breaches, it’s easy to see why endpoint security platforms have become must-haves in terms of protecting modern businesses.

Avoid threats across all ports and protocols by blocking links to malicious domains and content until a link is created or downloaded.
Web page gateways and their related agents have no complexity or latency. A great user experience is assured by fast connectivity and 100% uptime.

A simple, web-based made learning offers full visibility for all users, devices, and places for enhanced integration with visibility.
Use cloud-based monitoring to identify patterns and spot file activity irregularities, allowing you to monitor malicious behavior in the entire environment.

Malware should be deleted from all of the endpoints, like Windows PCs and laptops, Macs, phones, tablets, Linux devices, and servers.

To protect the users regardless of software, program, network, or location, use several protection layers across device, email, web, and cloud (SaaS) applications.

Shifting security boundaries that aren't clearly established necessitate adding new layers of security via endpoint protection.
End-user protection security software secures computers entering the corporate network with encryption and application control, allowing for greater security control on certain entry points and the detection and blocking of risky behaviors. Protecting data on endpoints and portable storage devices by encrypting it helps to avoid data leaks and failure. Data access prohibits end-users from running unwanted programs that might expose the network to vulnerabilities.
Endpoint security systems often use project management principles of protection, with a centrally controlled security solution securing the server and client applications deployed locally on each endpoint that connects to it. Some businesses follow a SaaS (Software as a Service) model, which helps them handle both central and peripheral security solutions remotely.
CSEs Endpoint Security offers the most complete, automated endpoint security infrastructure on the planet. As an on-site, hybrid, or cloud-based approach, the Symantec single-agent platform controls both conventional and mobile devices and optimizes security decisions through artificial intelligence. A centralized cloud management framework makes it easy to secure, track and respond to all emerging attacks that threaten the endpoints.
Our cloud solutions help the global enterprise achieve business goals.

We work to identify the clients IT problem and offer the best solution. Time and again,we face a situation that demands agility and the right set of talent that can solve technology issues.
Learn More
Not all projects are about innovation. Some are those that add a feather in our cap no matter what we deliver and how. It was typically a government project that involved a lot of roadblocks right.
Learn More
Being an expert IT solutions partner in the US and worldwide, we are committed to delivering results that drive business growth. Our team recently worked with Neil Hoosier & Associates to resolve.
Learn More
Introduction: As growth and evolution of early-stage cyber-attacks continue to move at a faster rate than ever, cybersecurity certificates have …

In today’s fast-paced digital landscape, businesses need an operating system that is secure, efficient, and built for modern workflows. Microsoft’s …
Continue reading “Why Upgrading to Windows 11 is a Game-Changer for Your Business”

Microsoft has announced a price increase for its Microsoft 365 services in 2025, impacting both business and personal users. With …
Continue reading “Understanding the 2025 Microsoft 365 Price Increase: What to Expect”

Windows 10 was a cornerstone for personal and enterprise computing for a decade. From the moment Microsoft launched the operating …
Continue reading “Windows 10 End of Support: Everything You Need to Know”