Comparing Azure Firewall with NSGs for Network Security
When businesses run work on a cloud service, they must keep an eye on and handle both as enterprises run their operations on a cloud service. They must monitor and manage all data flow for security purposes to implement Azure network security best practices.
Microsoft Azure offers two levels of protection for managing incoming and outgoing traffic:
- Azure Firewall Program
- Network Security Groups in Azure Firewall (NSGs)
Both services provide security but at varying levels of the network. Discover how each service is or the key features of Microsoft Azure network security and NSGs fairs for the businesses.
Azure Firewall
Azure offers layer 4 & 7 network security on a virtual network to protect the entire Windows Azure platform. The security policy relies entirely on Microsoft, and we build and configure the rules (a NAT rule, a network rule, and an application collection).
Creative options are configured to guarantee at least 99.99 percent availability. Also, cloud scalability can scale depending on the flow of traffic allowed in and return out.
Other top Microsoft Azure network security features include
- Implementation
- Outbound source network address translation (SNAT) support
- Filtering riles of Fully Qualified Domain Name
- FQDN tags
- In-Previews web categories
- Certification
- Inbound destination network address translation (DNAT) support
- Multiple public IP addresses
- Azure Service tags
- Threat intelligence and
- Logging of Azure Monitor
- Forced Tunnelling
What is a Network Security Group?
A network security gateway (NSG) is a Microsoft service that simplifies virtual network security by enforcing and controlling network traffic. NSGs are compatible with an Azure VM’s subnets and network interfaces.
NSGs are used to store security rules and provide a mechanism for activating a rule or gaining access to a control list. IT teams may use these rules to coordinate, process, and route various forms of network traffic. These rules, which filter both data traffic, reject or permit traffic based on the following five-tuple data:
- source
- source port
- destination
- destination port
- protocol
A comparison of Azure Firewall and NSGs
In comparison to NSGs, implementing Azure network security best practices enables looking at what each OSI layer defines. All this knowledge is essential for understanding how data moves through a network. Technically, it starts at layer 1, then to the application layer. At the OSI (Open Systems Interconnection) L3 and L4 level, NSG operates as a firewall, while Azure firewalls act as OSI firewalls.
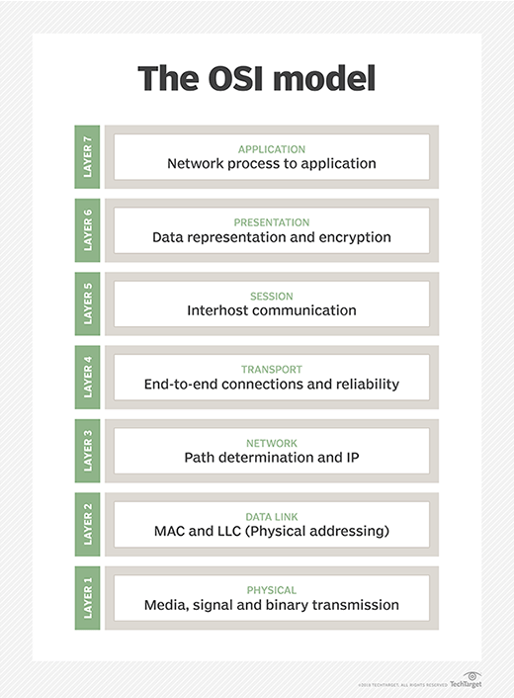
Although Microsoft Azure network security is a complex and versatile service that includes various features for traffic regulation, NSGs serve as a more simplistic firewall that filters traffic at the network layer. Azure virtual network firewall can analyze and filter traffic at the L3, L4, and L7 levels. Additionally, Azure Firewall supports threat intelligence-based scanning, which NSG does not.
Both alternatives identify network access controls using service tags. Service tags are groups of IP addresses associated with specific services that secure Azure resources and allow network isolation. In addition to NSGs, Azure Firewall supports device FQDN tags used in conjunction with application rules to enable necessary outbound traffic through the firewall.
Implementing Azure network security best practices will mean businesses using Azure firewall security to filter traffic to and from a VNet using its threat intellectual ability filtering capability. Usually, NSGs are used to secure traffic entering and exiting a subnet.
These two network security providers will work with the tandem to provide defense-in-depth network security, which entails implementing various defensive steps. This way, if one security measure fails, another will take its place.
Azure Firewall and NSG Comparison
NSG is a basic firewall. It is a solution described at the Network layer as a software-defined approach. Conversely, Azure has more protection, but it is much more complex. In addition to filtering and examining L3 and L4 traffic, it manages L7 and L7 traffic. It does the same job as an NSG, with additional features. The table seen below shows the options side-by-by-side:
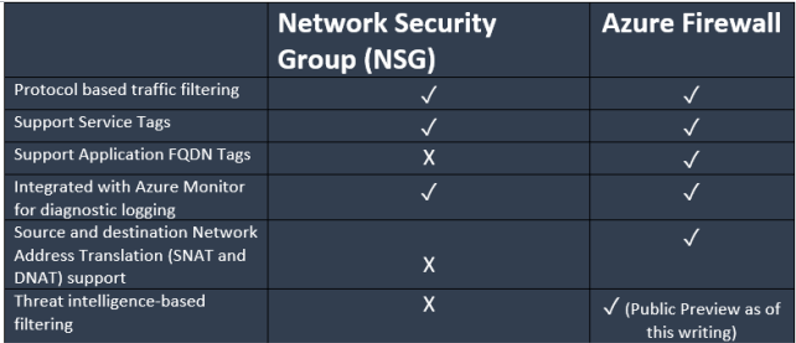
If you are not familiar with all the features mentioned above mentioned in the preceding map, the following meanings can help:
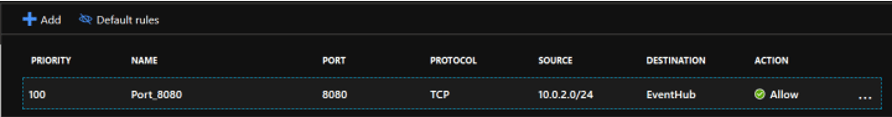
- Azure Key Vault, Container Registry, Data Lake, etc. Microsoft’s extensions cannot be customized. The more you know about these subjects, the better off you will be. This is an example of a Service tag that I have applied to a publisher/subscriber NSG delivered in an outbound rule. A more advanced implementation of this same rule can be done in Azure Security.
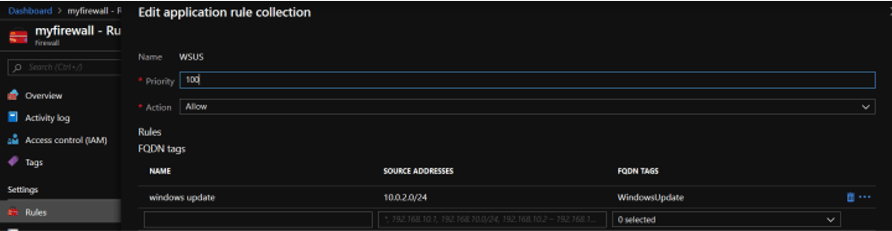
- FQDN Tags – denote a set of entirely eligible domain names associated with Microsoft services such as Windows Update or Azure Backup. They, like Service tags, are managed by Microsoft and are not customizable. There are significantly fewer FQDN tags than there are Service tags.
Here is an example of an FQDN tag you can use to implement Azure virtual network best practices for the Windows Update. This eliminates the need to create separate framework rules for each of the various Windows Update endpoints. There is only one tag that can be used to govern them all!
- Azure Firewall has a function called SNAT – Source Network Address Translation. It is possible to customize Azure Firewall with a Default IP address (PIP) that can mask the IP address of Azure Resources that communicate with the Firewall through the Firewall.
- DNAT – Source Destination Address Translation translates incoming traffic to the firewall’s public IP address to the VNet’s Private IP addresses.
Azure Firewall and NSG in Conjunction
We have discovered that NSGs and Azure Firewalls fit well together and are not contradictory. There is a reason you can use NSGs for traffic within or outside of a subnet: network segmentation. a good illustration will be a jump box that needs to provide RDP connectivity to a subset of the subnet: Azure Application Gateway protects the security of a VNet from the outside.
Due to this, it should be placed in a separate virtual network, as this does not mix with other tools. Automated scaling on-demand Microsoft azure network security is highly available is always available and scales depending on workload.
Both may be used in a Hub-spoke VNet environment that receives incoming traffic from the outside.
Consider the diagram below:
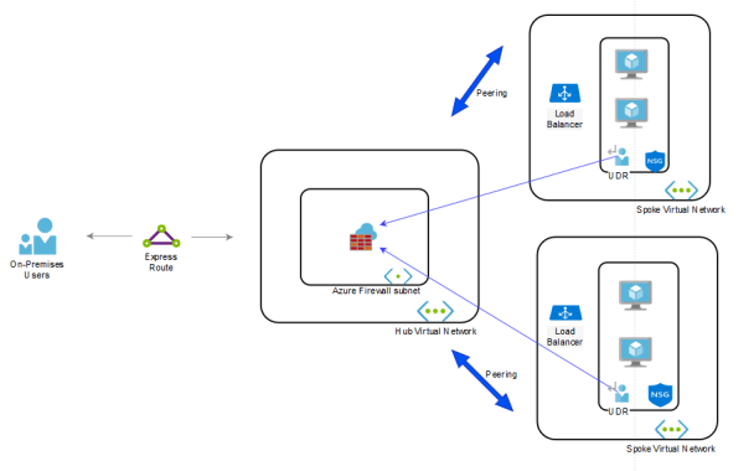
Peering between the above Azure Fire hub and two spoke VNet objects. Network Vnets are related but have a Subnet Gateway (SG) that points to the Azure Firewall. In addition, Azure Firewall protects the Azure Virtual Network for inbound and outbound security and handles the VNet inbound and outbound traffic. Here’s where features like SNAT and DNAT are beneficial. If your network has only one subnet, NSGs are adequate to guard your network.


