Defending Against Insider Threats: How Can Businesses Protect Themselves from Insider Threats?
An insider threat is a security danger that originates from within a company and typically involves a current or former employee or partner who has access to critical information and abuses that access. Most security measures are designed to combat external attacks, and most businesses aren’t always ready at detecting internal dangers.

Eye-Opening Insider Cyber Threat Statistics
- Insider attacks are growing more prevalent, according to 68% of companies.
- Since shifting to the cloud, 56% of organizations say detecting insider assaults has gotten significantly more complex.
Modern risk pain points
Understanding the types of risks in today’s workplace is the first step in managing and minimizing risk in your firm. Some risks are influenced by events and variables outside one’s control. Internal occurrences and user activities are responsible for other dangers, which can be reduced or prevented. Risks from unlawful, unsuitable, unapproved, or unethical activities and acts by users in your organization are just a few instances. A wide range of internal dangers from users are included in these behaviors:
- Data spillage and sensitive data leaks
- Violations of confidentiality
- Theft of intellectual property (IP)
- Fraud
- Insider trading
- Violations of regulatory compliance
Users in the modern workplace have access to a wide range of platforms and services for creating, managing, and sharing data. Organizations typically have limited resources and tools to detect and mitigate organization-wide risks while simultaneously adhering to user privacy regulations.
Insider Threats: What They Are and How They Can Affect You
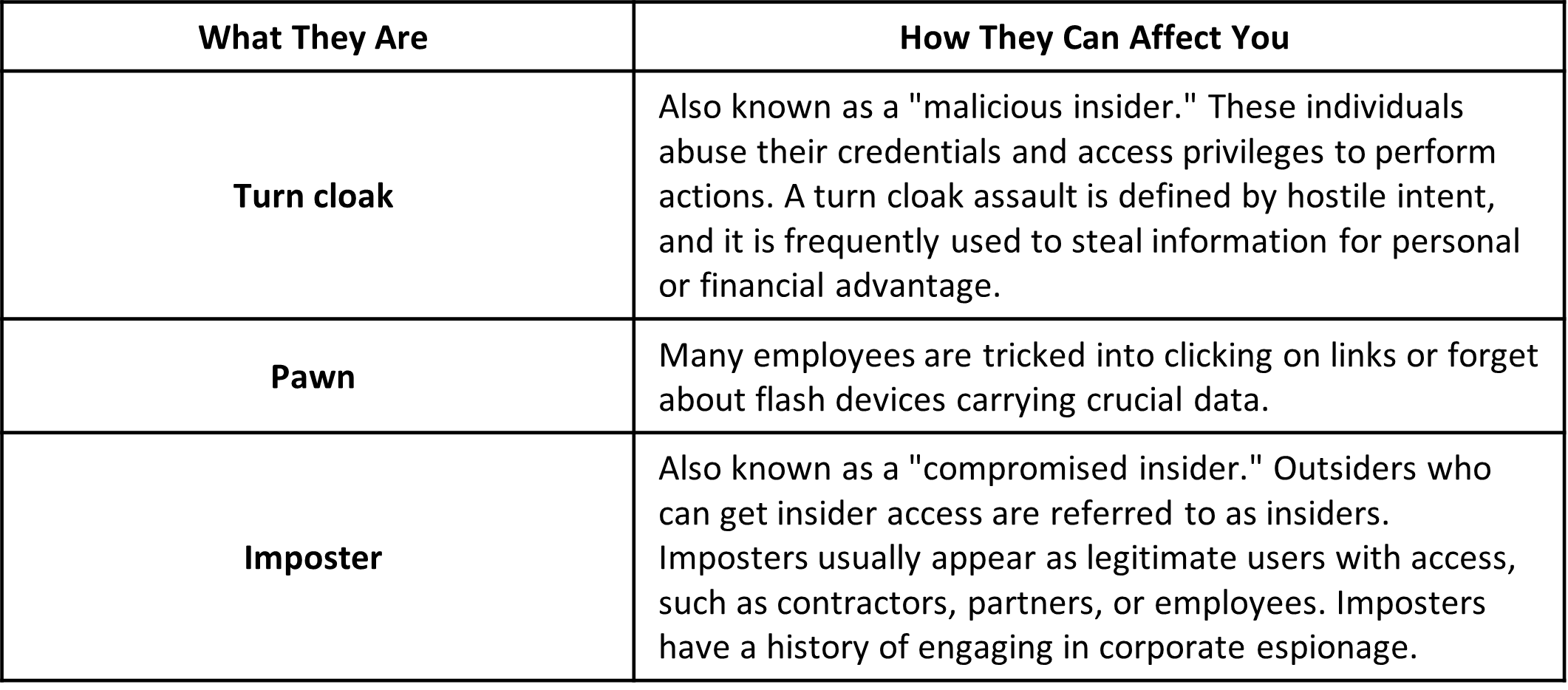
Costs of Insider Threats
An insider threat assault might result in significant financial damages for a company. According to research, insider threats of the pawn sort can cost an average of $307,111. When pawns are used in the attack, the average rises to $756,760. According to the survey, imposters might quadruple the charges to $871,686 on average. Another concerning finding was the average time it takes to contain insider occurrences, which was 77 days.
It makes no difference whether an imposter or a pawn caused the data loss in defense. What matters is that sensitive information is continually safeguarded, regardless of who has access to it. The primary issue is that all three insiders are already operating within the network. Organizations must monitor user activity and behavior to protect their data and learn patterns that distinguish between normal authorized behavior and malicious behavior. This can aid in detecting and prompt responses to any form of insider threat.
Insider Threat Mitigation Strategies
Make use of risk assessments
The risk assessment must be used in an enterprise-wide information security landscape to identify essential assets and build a risk management method to protect those assets from insiders and outsiders.
Technical Restrictions
Technical controls, which are designed to analyze and identify questionable user behavior, can be set up by organizations. Technical controls have grown in popularity, primarily due to their ability to compare user behavior to previous acts and detect abnormal behaviors. Network traffic, file system access, endpoint activity, and logins, for example, can all be compared using technological controls.
Insider threat detection can also be done using a company’s security technology stack. SIEM systems, for example, may spot anomalies across whole networks and issue alerts when malicious insider activity is identified. In contrast, network, and endpoint Data Loss Prevention (DLP) solutions can alert enterprises when massive files mysteriously disappear from corporate servers.
Policies and regulations should be clearly documented and consistently enforced
Each security software must have its management policy and configuration documentation.
- General data protection regulations
- An incident response policy
- A third-party access policy
- An account management policy
- A user monitoring policy
- A password management policy
Install security software and hardware
Install and setup the software listed below:
- Active Directory
- Endpoint protection system
- Intrusion prevention system
- Intrusion detection system
- Web filtering solution
- Traffic monitoring software
- Spam filter
- Privileged access management system
- Encryption software
- Password management policy and system with at least two-factor authentication
- Call manager
- Data loss prevention system
Identifying potential risks with analytics
Without establishing any insider risk controls, insider risk analytics allows you to assess potential insider risks in your firm. This assessment can assist your company in identifying potential areas of increased user risk and determining the type and breadth of insider risk management policies that should be implemented. This assessment may also assist you in deciding whether further licensing is required or whether existing insider risk measures should be improved in the future.
Our Approach to Insider risk management
Our approach to insider risk management assists you in identifying, investigating, and responding to internal threats in your company. You may leverage actionable insights to swiftly identify and act on problematic behavior with tailored policy templates, extensive activity signaling across the Microsoft 365 service, and alert and case management capabilities.
We assist you with Insider risk management policies by using pre-defined templates and policy conditions that specify which your firm examines triggering events and risk indicators. These factors include how risk indicators are utilized to generate warnings, covered by the policy, which services are prioritized, and how long the monitoring will last.
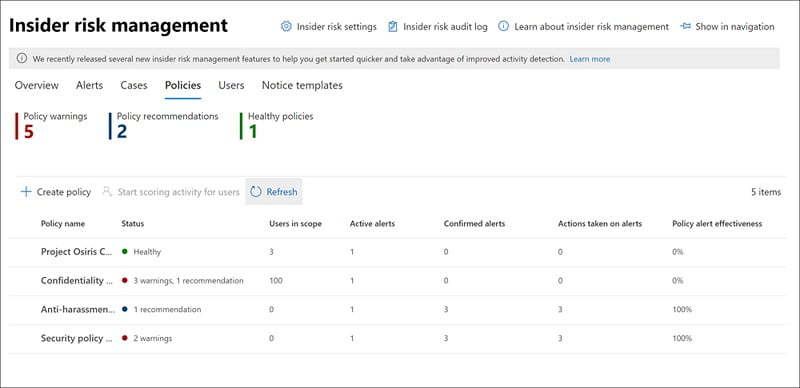
We’ll configure the alerts, which will be generated automatically when risk indicators fit policy conditions and are presented in the Alerts dashboard. This dashboard gives you a rapid overview of all alerts that need to be reviewed, opens signs over time, and alerts your company’s data.
Insider threats are increasingly becoming a significant source of security breaches. As phishing schemes become increasingly widespread and sophisticated, even high-level stakeholders are being duped into becoming pawns. Organizations might suffer substantial losses when users with high privilege levels become pawns. Insider risk must be mitigated before it becomes a threat, occurrence, or incident to improve overall security and reduce organizational risk. Talk to our Cybersecurity expert today before it’s too late.


