Hire the Top Managed IT Service Providers to Help Humanize Your Digital Security
National security, business security, energy security, food security… They’re all the same. While Iowa grain co-op, New Cooperative, may seem far removed from the capital of the U.S. government, a ransomware attack threatens food security in the Midwest. The cyberattack, and its consequences, are a concern for everyone across the country, not just local individuals.
JBS, the world’s largest meatpacker located in Brazil, suffered a ransomware attack a few months before the $5.9 million attacks on New Cooperative, disrupting meat production in North America and Australia during grilling season. Wholesale beef prices in the United States increased more than 1%, according to USDA.
Cybercriminals can target more than only the agricultural industry to jeopardize American national security. In May, Colonial Pipeline was hampered by yet another ransomware attack, which caused fuel service to be disrupted for six days across much of the east coast. For the decryption key, the oil pipeline eventually paid $4.4 million.
Furthermore, industries are more intensively targeted because of their widespread effects on large sections of the population in the United States. Essential service markets face increased threats and bear greater responsibilities for securing vulnerabilities.
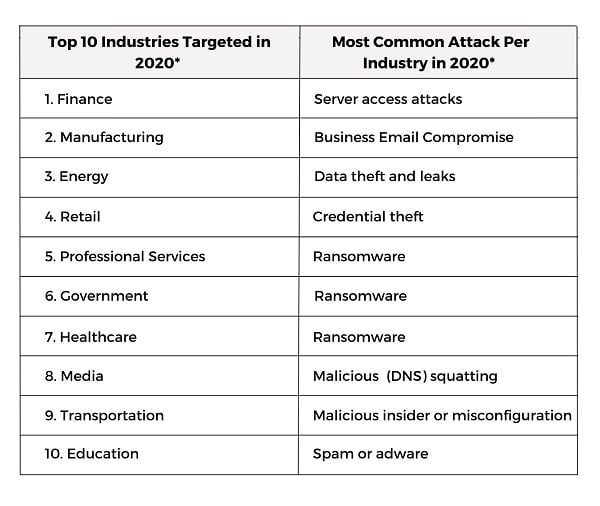
The increasing frequency and sophistication of cyberattacks is a problem for everyone, not just businesses. They are a direct threat to the United States’ security, as well as the privacy, health, and financial well-being of its citizens. The importance of cybercrime cannot be overstated, and it is on the minds of the country’s senior officials.
Here’s a list of effective tactics to build your business’ multilayered cybersecurity:
- Detection and Response to Endpoints
- Patching Windows and Third-Party Patching
- Cloud Email Security per User
- Cybersecurity Security Awareness Training
- DNS Security
- Incident Response and Remediation
- Health Check and Review
- Vulnerability Network Edge Scans
- Security Management of Information and Events (SIEM)
- Correlation and Aggregation of Event Logs
- 24*7*365 Monitoring
Computer Solutions East has developed managed Comprehensive cybersecurity services that include user-focused tactics and carefully selected solutions to defend, identify, and respond to cyber risks and threats that target your business. Computer Solutions East provides the cybersecurity compliance services to establish and strengthen your cybersecurity and award-winning managed service provider. We safeguard your business and consumers.
How Can We Assist You in Maximizing Your Cybersecurity?
Vulnerability Management – It appears that many businesses believe they can buy vulnerability management software, scan their environments, and then check the compliance box. If only everything were that simple. While a threat detection tool is essential for alerting managed service providers to security flaws in their environment, the technology alone cannot prevent intrusions. To get the most out of these solutions, companies must enlist the help of best-managed IT service providers or automated processes to close security vulnerabilities.
Managed Security Operations - Many companies hire third-party managed security service providers to monitor their networks, provide security intelligence and event planning services, and run their security operations centers. This makes sense because some organizations cannot afford to staff their internal security operations with multiple security analysts. However, there is a common set-it-and-forget-it approach here as well. As a result, when a security management company uncovers a cybersecurity incident, it usually informs the company.

Only a small number of security management companies, however, help with cleanup. So, what’s the common thread here? First, do your homework, understand what you’re buying, and be ready to refill current assets as needed.
Inventory Control – To ensure that organizations track, monitor, manage, and safeguard their IT assets, IT asset management technologies should be used effectively. They miss significant chunks of their best-managed IT service providers despite a bit of setup error. Firms that fail to configure these tools to specified IP ranges will not have their entire organization’s assets analyzed.
Identity and Access Management – Identity and access management solutions such as two-factor authentication ensure that only authorized individuals have access to sensitive systems and data, especially given the recent rise in remote work. These strategies, however, will be useless unless they are implemented across a company by top IT-managed service providers. Some firms, for example, may ensure that managed solutions providers for MFA are in place so that they can use their proxy server tunnels.
A third party, such as CSE as a best managed IT service provider, can operate as an objective observer, aiding businesses in assessing current security environments against industry standards and best practices and recommending areas for improvement. Frequently, companies prioritize cybersecurity only after a costly incident has occurred. They may, however, avert severe damage to their consumer data, intellectual property, and reputation by being proactive.
Hire the best managed IT service providers to assist in humanizing your digital security by ensuring that your staff understands how they can contribute. Any slight change in your approach to anything can make a big difference.


